
technology technology
Your web browser is an ecosystem of its own. It stores your passwords, search history, financial details like credit card numbers, addresses and more. Just like how malicious apps and services can compromise data on your phone or PC, malicious extensions can expose the data stored in your browser.
There are a ton of extensions out there that do more harm than good. In fact, security researchers have just found a dangerous new campaign that is going after browser extensions. So far, around 36 extensions have been compromised, putting over 2.6 million Chrome users at risk of having their browsing data and account credentials exposed.
I’M GIVING AWAY THE LATEST & GREATEST AIRPODS PRO 2
Enter the giveaway by signing up for my free newsletter.

A person using a Chrome browser extension (Kurt “CyberGuy” Knutsson)
How hackers are targeting browser extensions
Hackers are exploiting browser extensions as a gateway to steal sensitive user data through a variety of methods. These compromised extensions are exposing over 2.6 million users to data exposure and credential theft, as reported by The Hacker News.
One common attack involves phishing campaigns targeting the publishers of legitimate extensions on platforms like the Chrome Web Store. In these campaigns, attackers trick developers into granting permissions to malicious applications, which then insert harmful code into popular extensions. This code can steal cookies, access tokens and other user data.
The first company to shed light on the campaign was cybersecurity firm Cyberhaven, one of whose employees were targeted by a phishing attack on December 24, allowing the threat actors to publish a malicious version of the extension.
Once these malicious extensions are published and pass the Chrome Web Store’s security review, they are made available to millions of users, putting them at risk of data theft. Attackers can use these extensions to exfiltrate browsing data, monitor user activity and even bypass security measures such as two-factor authentication.
In some cases, developers themselves may unknowingly include data-gathering code as part of a monetization software development kit, which stealthily exfiltrates detailed browsing data. This makes it difficult to determine whether a compromise is the result of a hacking campaign or an intentional inclusion by the developer.

Image of a Chrome browser on a cellphone (Kurt “CyberGuy” Knutsson)
MASSIVE SECURITY FLAW PUTS MOST POPULAR BROWSERS AT RISK ON MAC
Remove these extensions from your web browser
The browser extension security platform Secure Annex has launched its own investigation into this hacking campaign. So far, it has uncovered over twenty additional compromised extensions, which are listed below. If you have any of the compromised extensions listed in Secure Annex’s investigation installed on your browser, it’s essential to remove them immediately to protect your data.
- AI Assistant – ChatGPT and Gemini for Chrome
- Bard AI Chat Extension
- GPT 4 Summary with OpenAI
- Search Copilot AI Assistant for Chrome
- TinaMInd AI Assistant
- Wayin AI
- VPNCity
- Internxt VPN
- Vindoz Flex Video Recorder
- VidHelper Video Downloader
- Bookmark Favicon Changer
- Castorus
- Uvoice
- Reader Mode
- Parrot Talks
- Primus
- Tackker – online keylogger tool
- AI Shop Buddy
- Sort by Oldest
- Rewards Search Automator
- ChatGPT Assistant – Smart Search
- Keyboard History Recorder
- Email Hunter
- Visual Effects for Google Meet
- Earny – Up to 20% Cash Back
- Cyberhaven security extension V3
- GraphQL Network Inspector
- Vidnoz Flex – Video recorder & Video share
- YesCaptcha assistant
- Proxy SwitchyOmega (V3)
- ChatGPT App
- Web Mirror
- Hi AI
Keeping these extensions installed is a serious risk since hackers can still access your data even if the malicious version has been taken down from the Chrome Web Store. Secure Annex is still investigating and has shared a public Google Sheet with details about the malicious extensions it has found so far, like whether they’ve been updated or removed. They’re also adding new extensions to the list as they discover them.
WORLD’S LARGEST STOLEN PASSWORD DATABASE UPLOADED TO CRIMINAL FORUM
How to remove an extension from Google Chrome
If you have installed one of the above-mentioned extensions on your browser, remove it as soon as possible. To remove an extension from Google Chrome, follow these steps:
- Open Chrome and click the icon that looks like a piece of a puzzle. You’ll find it in the top-right corner of the browser.
- You can see all the active extensions now. Click the three dots icon next to the extension you want to remove and select Remove from Chrome.
- Click Remove to confirm
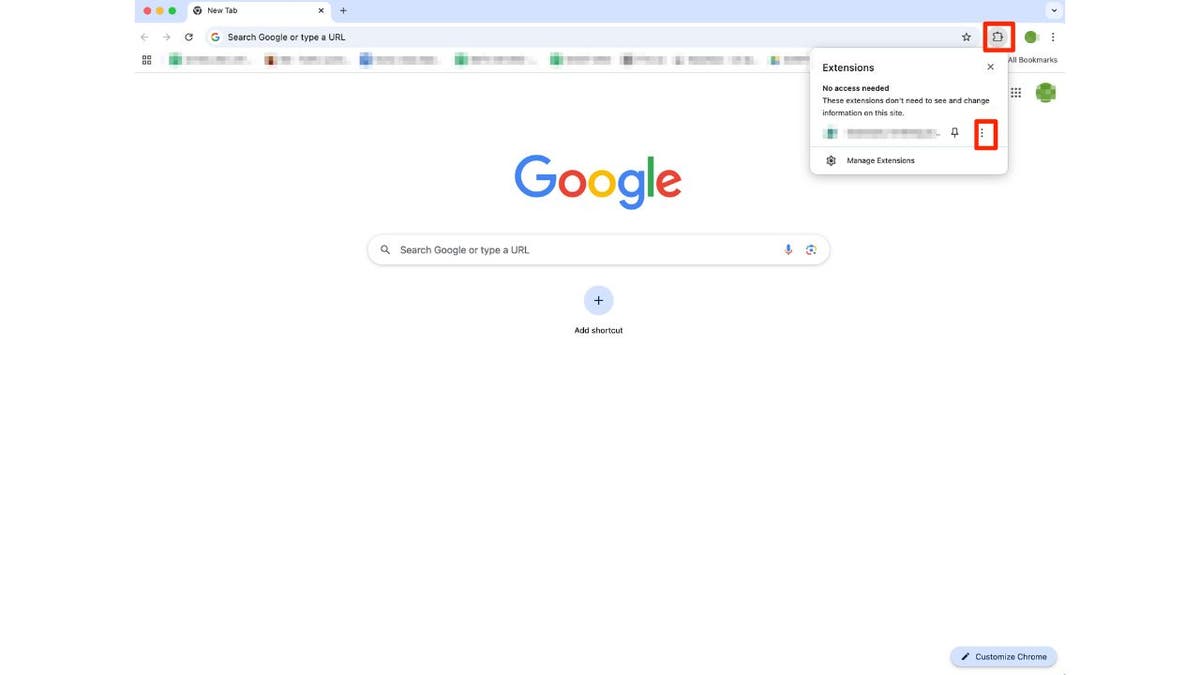
Steps to remove an extension from Google Chrome (Kurt “CyberGuy” Knutsson)
BEST ANTIVIRUS FOR MAC, PC, IPHONES AND ANDROIDS – CYBERGUY PICKS
7 ways to stay safe from malicious software
1) Verify emails and links before clicking: Many attacks begin with phishing emails that impersonate trusted entities like Google Chrome Web Store Developer Support. These emails often create a false sense of urgency, urging you to click on malicious links. Always verify the sender’s email address and avoid clicking on links without double-checking their authenticity. When in doubt, go directly to the official website rather than using a provided link.
2) Use strong antivirus software: Having strong antivirus software is an essential line of defense against malicious software. These tools can detect and block malicious code, even if it has been embedded in browser extensions. The best way to safeguard yourself from malicious links that install strong malware, potentially accessing your private information, is to have antivirus software installed on all your devices. This protection can also alert you to phishing emails and ransomware scams, keeping your personal information and digital assets safe. Get my picks for the best 2025 antivirus protection winners for your Windows, Mac, Android and iOS devices.
3) Limit extension permissions: Be cautious about the permissions you grant to browser extensions. Many require access to sensitive data like browsing history, cookies or account information, but not all requests are necessary. Review what each extension asks for and deny permissions that seem excessive. If possible, opt for extensions with limited access to ensure your data remains protected.
4) Limit the number of extensions: Only install extensions that are genuinely needed and regularly review and uninstall those no longer in use.
5) Keep your browser updated: Always update your browser to the latest version. Updates often include critical security patches that protect against vulnerabilities exploited by malicious software. Using an outdated browser increases the risk of being targeted by attacks that could have been prevented with a simple update. Enable automatic updates to ensure you’re always protected. If you are unsure how to update your browser, check out my detailed guide for Google Chrome.
6) Regularly audit your extensions: Conduct periodic reviews of installed extensions and remove any that are unnecessary or pose potential security risks.
7) Report suspicious extensions: If you encounter a suspicious extension, report it to the official browser extension marketplace.
SUBSCRIBE TO KURT’S YOUTUBE CHANNEL FOR QUICK VIDEO TIPS ON HOW TO WORK ALL OF YOUR TECH DEVICES
Kurt’s key takeaway
Hackers are getting smarter, and browser extensions have become a new favorite target for stealing sensitive data. The discovery of over 35 compromised Chrome extensions, putting 2.6 million users at risk, is a wake-up call for everyone. Removing suspicious extensions is an essential step to protect your data. This also puts Google’s Chrome Web Store review process under scrutiny, proving that even trusted platforms can be exploited.
How often do you review and remove unused or suspicious browser extensions? Let us know by writing us at Cyberguy.com/Contact.
For more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you’d like us to cover.
Follow Kurt on his social channels:
Answers to the most asked CyberGuy questions:
New from Kurt:
Copyright 2024 CyberGuy.com. All rights reserved.










